Mobile Interface Outline Set of 9 Pictograms of stamp document cryptography certificate mac Editable Vector Design Elements 19241819 Vector Art at Vecteezy
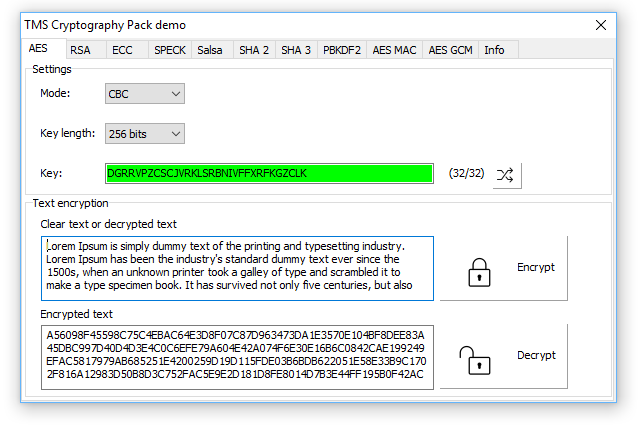
TMS Cryptography Pack Software library that provides various algorithms used to encrypt, sign and hash data.

Prof Bill Buchanan OBE on LinkedIn: So what's a MAC in cryptography? A MAC (message authentication code)…
GitHub - NilFoundation/crypto3-mac: Message authentication codes for =nil; Crypto3 cryptography suite

Attacks on the RawCBC-MAC if the final step of encrypting with a second key isn't done - Cryptography Stack Exchange